Information and communication infrastructures, such as the Internet, have become a crucial part of today's life, and they penetrate all aspects of our society. Relying on the correct functionality of the underlying computer systems, businesses carry out transactions, governments offer services to the public, and users access news and entertainment. Unfortunately, our computer infrastructure is exposed to a steadily growing onslaught carried out by attackers who seek to exploit weaknesses to make a financial profit or who simply wreck havoc with the goal of embarrass or blackmail their victims. To defend our infrastructure against these attackers, we require novel and innovative approaches to make our systems secure.
The Center for Cybersecurity has been created at UCSB to foster research on Internet security and support collaboration and sharing of ideas between UCSB faculty and industrial partners. In this event, several faculty members who are affiliates of the Center for Cybersecurity present their research in security and discuss their approach with members of the industry.
The talks are introduced by a keynote by Mike Reavey, from Microsoft, and are interspersed with opportunities to socialize and network with members of the Computer Science faculty.
Program
The meeting will be held at UCSB, in Ealings Hall, room 1601, on May 31st, 2011, from 9:30am to 4:30pm.
- 9:30-10:00 Check-in and Registration
- 10:00-11:00 Keynote: Evolving the Security Capability in the Microsoft Trustworthy Computing Division (Mike Reavey, Director, Microsoft Security Response Center)
- 11:00-11:30 Large-scale Web Threat Analysis: Challenges and Pitfalls (Giovanni Vigna)
- 11:30-noon Precise, large-scale malware analysis (Chris Kruegel)
- noon-1:30 Lunch Break
- 1:30-2:00 Eliminating Bugs in MVC-Style Web Applications (Tevfik Bultan)
- 2:00-2:30 Towards a Sound Hardware Foundation for System Security (Tim Sherwood)
- 2:30-3:00 Holistic Cyber Situation Awareness (Richard Kemmerer)
- 3:00-4:30 Mixer and wine reception
Keynote abstract
Evolving the Security Capability in the Microsoft Trustworthy Computing Division
Microsoft formalized its security engineering and incident response processes in reaction to the dramatic changes in the security landscape and the threat environment. Mike Reavey will recount the maturing of the Microsoft security capability to its current focus on Collaborative Defense and highlight lessons, methodologies, strategies that organizations and software developers can employ to help them meeting the continuing challenge of the evolving security landscape.
Keynote presenter's bio
Mike Reavey is the director of the Microsoft Security Response Center (MSRC) in the Trustworthy Computing Group at Microsoft Corp. In this role, Reavey leads Microsoft's security response team in detecting and addressing software vulnerabilities in Microsoft products. Additionally, Reavey engages with cross-Microsoft product groups and the external researcher community to proactively identify security threats and help keep customers protected. Reavey has worked with the MSRC since 2003, continually aiming to improve the team's response framework. Most notably, Reavey was very involved in resolving the Zotob, Sasser and Blaster virus outbreaks. Prior to joining Microsoft, Reavey was a team leader for the Air Force Communications Agency and the 92nd Information Warfare Squadron in the U.S. Air Force. In this role, he worked to secure and optimize global air force networks. Reavey was drawn to Microsoft because of the company's ability to impact change in the security landscape, as well as Microsoft's focus on continually improving product security. Additionally, he was intrigued by the reality that security fundamentally helps society as a whole, a notion that he also felt while working in the military. Diversity of challenges, smart minds, dedicated colleagues and the ability to work directly with the researcher community has kept Reavey passionate about this space. Reavey is a Florida native. While he misses the sun, opportunities and people have kept him loving Seattle for the past seven years.
Academic Representatives
 |
Tevfik Bultan is a Professor of Computer Science at the University of California, Santa Barbara. His research interests include web software dependability, static string analysis, model checking, and software engineering. He founded and chaired the Workshop on Testing, Analysis and Verification of Web Software (TAV-WEB). He was a keynote speaker at the ACM Workshop on Program Analysis for Software Tools and Engineering (PASTE), International Conference on Concurrency Theory (CONCUR), and ACM-IEEE International Conference on Formal Methods and Models for Codesign (MEMOCODE). He is the recipient of an NSF CAREER award, and an ACM SIGSOFT distinguished paper award. |
 |
Fred Chong is the Director of Computer Engineering and a Professor of Computer Science at the University of California at Santa Barbara. He also directs the Greenscale Center for Energy-Efficient Computing, which involves over 20 multi-disciplinary faculty. Chong received his Ph.D. from MIT in 1996 and was a faculty member and Chancellor's fellow at UC Davis from 1997-2005. He is a recipient of the NSF CAREER award and the DARPATech Most Significant Technical Achievement award. His research interests include emerging technologies for computing, multicore and embedded architectures, computer security, and sustainable computing. |
 |
Richard A. Kemmerer is the Computer Science Leadership Professor and a past Department Chair of the Department of Computer Science at UCSB. His research interests include formal verification of systems, computer and network security, electronic voting system security, intrusion detection, and the cyber underground economy. He is author of the book Formal Specification and Verification of an Operating System Security Kernel. Dr. Kemmerer is a Fellow of the IEEE Computer Society, a Fellow of the Association for Computing Machinery, and the 2007 recipient of the Applied Security Associates Distinguished Practitioner Award. He also serves on Microsoft's Trustworthy Computing Academic Advisory Board. |
 |
Christopher Kruegel is the Eugene Aas Associate Professor in the Computer Science Department at the University of California, Santa Barbara. His research interests are computer and communications security, with an emphasis on malicious code analysis and detection, web security, and intrusion detection. He has published more than 70 conference and journal papers and is a recent recipient of the NSF CAREER Award. Moreover, he served as the program chair of the 10th Symposium on Recent Advances in Intrusion Detection (RAID) and the 4th ACM Workshop on Rapid Malcode (WORM), and he is currently an associate editor for the Journal of Computer Security. |
 |
Tim Sherwood is an Associate Professor of Computer Science with a research interest in hardware security, high assurance design, streaming analysis, and computer architecture. On 4 separate occasions his work has been selected by IEEE Micro as a "Top-Pick of the year", he is a recipient of an NSF Career Award, and has won numerous teaching awards including the Northrop Grumman Excellence in Teaching Award. Prior to joining UCSB, he graduated with a B.S. in Computer Science and Engineering from UC Davis (1998), and received his M.S. and Ph.D. in the same from UC San Diego (2003). |
 |
Giovanni Vigna is a Professor in the Department of Computer Science at the University of California in Santa Barbara. His current research interests include malware analysis, web security, vulnerability assessment, and intrusion detection. He has been the Program Chair of the International Symposium on Recent Advances in Intrusion Detection (RAID 2003), of the ISOC Symposium on Network and Distributed Systems Security (NDSS 2009), of the IEEE Symposium on Security and Privacy (S&P 2010). He is known for organizing and running an inter-university Capture The Flag hacking contest, called iCTF, that every year involves dozens of institutions around the world. |
 |
Xifeng Yan is an assistant professor at the University of California at Santa Barbara. He holds the Venkatesh Narayanamurti Chair in Computer Science. He received his Ph.D. degree in Computer Science from the University of Illinois at Urbana-Champaign in 2006. He was a research staff member at the IBM T. J. Watson Research Center between 2006 and 2008. He has been working on modeling, managing, and mining large-scale graphs in bioinformatics, social networks, the Web, and computer systems. His works were extensively referenced, with over 4,000 citations per Google Scholar. He received NSF CAREER Award. |
 |
Ben Zhao is an Associate Professor in the Computer Science department at UCSB. His research interests include algorithms, protocols and security for Internet-scale networks and distributed systems. Lately, he has been gathering and analyzing million-node graphs from online social networks, and devising ways to protect user privacy in online and mobile social networks. He has been Program Co-chair for the International Workshop on Peer-to-Peer Systems (IPTPS 2006) and for the IEEE International Conference on Peer-to-Peer Computing (P2P 2010), and is a recipient of the NSF Career, MIT TR-35 Young Innovator and ComputerWorld Top 40 Tech Innovator awards. |
Directions
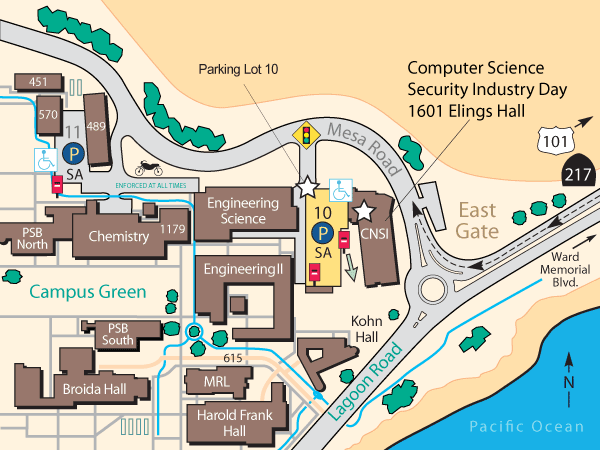
Once you arrive in the parking garage 10, please park on the top floor. There is an area reserved for the event. Attendants will be required to obtain a permit.
To purchase a permit, go to the red parking vendor machine (Pay Station) on the fourth floor, located near the north or south elevators, and follow the screen instructions. Please purchase an all-day pass, which costs $8. There is no need to return to your car, but you have to note and use your parking space number. We strongly encourage you to bring cash in the correct amount, since the vending machine does not give change. Vending machines will SOMETIMES accept credit cards and ATM cards.